Malware Maladies, Beverly Rosenbaum
Malware Attacks Increase Exponentially
Security experts reported an “explosion” of malware in 2008.
PandaLabs, the malware research laboratory of Panda Security in Spain, reported that Trojans designed to steal bank accounts, passwords, and other confidential data are the leading cause of malware infections (70%). And there’s an increase in rogue anti-malware programs as well. So after the Trojans themselves trick you, bogus removal offers cheat you again.
 In the first eight months of 2008, PandaLabs detected 22,000 new infections per day. That’s more malware than the combined total received in the previous 17 years of the company’s existence. They’ve classified these threats into 2 major categories, classic malware and cybercrime. Examples of classic malware are infection from viruses, worms, Trojans, and rootkits; while cybercrime includes attempts to defraud users with spyware, spam, phishing, and other bots that allow hackers to control infected machines. In the first eight months of 2008, PandaLabs detected 22,000 new infections per day. That’s more malware than the combined total received in the previous 17 years of the company’s existence. They’ve classified these threats into 2 major categories, classic malware and cybercrime. Examples of classic malware are infection from viruses, worms, Trojans, and rootkits; while cybercrime includes attempts to defraud users with spyware, spam, phishing, and other bots that allow hackers to control infected machines.
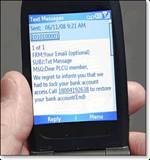
However, it appears that the newest threats contain elements from both categories. Recently, unsolicited text messages began targeting smart phones and PDAs. This form of “phishing” is called “SMiShing” because it uses the cell phone Short Message Service (SMS), or text messaging, to reach users of those devices and trick them into revealing personal banking data by phone or downloading malware from the Internet. Once infected, this adds an even greater risk to corporate networks, as use of these devices increases. To avoid being fooled, you should remember that banks and credit card companies would never contact you in this way or ask you to reveal confidential information over the phone or on a web site.
Creative Social Engineering
 Cyber-criminals are always thinking of new ways to get past users’ careful judgment and lure them into malicious domains. In North Dakota, they used car windshields as the attack vector in a phony parking ticket scam, instructing the car owners to visit a web site regarding parking fines. The site was a known malware drop. To find photos of their car, they were given a link to download what appeared to be a picture search toolbar that actually triggered the installation of a Trojan and malicious Browser Helper Object (BHO). What happens next is typical: once the user reboots the system and connects to the Internet, a message box appears alerting them of a malware infection and directing them to a website displaying fake security alerts. Then the unsuspecting user is prompted to download a Trojan disguised as anti-malware removal program, sometimes even requiring payment! The malware is not removed, but instead remains hidden until a later time when it can transmit personal information to an Internet server or direct infected computers to each send hundreds of SPAM emails as part of a huge botnet. Cyber-criminals are always thinking of new ways to get past users’ careful judgment and lure them into malicious domains. In North Dakota, they used car windshields as the attack vector in a phony parking ticket scam, instructing the car owners to visit a web site regarding parking fines. The site was a known malware drop. To find photos of their car, they were given a link to download what appeared to be a picture search toolbar that actually triggered the installation of a Trojan and malicious Browser Helper Object (BHO). What happens next is typical: once the user reboots the system and connects to the Internet, a message box appears alerting them of a malware infection and directing them to a website displaying fake security alerts. Then the unsuspecting user is prompted to download a Trojan disguised as anti-malware removal program, sometimes even requiring payment! The malware is not removed, but instead remains hidden until a later time when it can transmit personal information to an Internet server or direct infected computers to each send hundreds of SPAM emails as part of a huge botnet.
The latest social network attacked in an attempt to distribute malware is the popular bookmarking service Digg.com. Security researchers believe that fake news stories and malicious comments to legitimate entries have been posted there for more than a year. Over 500,000 comments have been found to contain malicious links, most leading to malware disguised as a video codec. Attackers have also invaded such services as Google Video, Picasa Web Albums, LinkedIn, Twitter, and Facebook, where they can reach many potential victims from the large pool of daily visitors.
Conficker Worm is Latest Concern
 Not since 2004’s Sasser Worm has anything spread like the newest threat. Panda Security estimates Conficker has now infected 1 in 16 PCs worldwide, calling the worm a new “digital plague.” Last month the number of systems infected by the Conficker worm had already exceeded 10 million, and security experts are concerned about the 350 million machines that are still vulnerable because updates have not been kept current. Also known as Downadup or Kido, this worm spreads by exploiting a critical vulnerability in the Windows RPC Server Service of XP and Vista, one for which Microsoft issued an out-of-band patch in October 2008. Those systems at greatest risk are XP with Service Pack 2 or 3, which account for most of Windows’ market share. Not since 2004’s Sasser Worm has anything spread like the newest threat. Panda Security estimates Conficker has now infected 1 in 16 PCs worldwide, calling the worm a new “digital plague.” Last month the number of systems infected by the Conficker worm had already exceeded 10 million, and security experts are concerned about the 350 million machines that are still vulnerable because updates have not been kept current. Also known as Downadup or Kido, this worm spreads by exploiting a critical vulnerability in the Windows RPC Server Service of XP and Vista, one for which Microsoft issued an out-of-band patch in October 2008. Those systems at greatest risk are XP with Service Pack 2 or 3, which account for most of Windows’ market share.
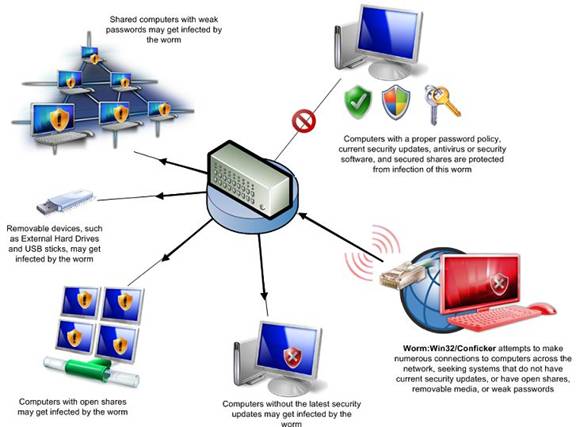
Several Conficker variants are infecting networks and spreading through file sharing and removable USB drives, where the worm executes automatically when the Autorun feature is enabled. It avoids detection by removing access rights of the user and disabling Windows updates. The following diagram, provided by Microsoft at www.microsoft.com/protect/images/viruses/diagram.jpg, shows the complex distribution of this worm, as it infects PCs in one of three ways: through file sharing, by brute force attack on weak passwords, and via USB removable drives.
The antivirus company F-Secure speculates that Conficker’s author is Ukrainian, because one of the worm’s first actions is to check if a computer has a Ukrainian-formatted keyboard. If it does, it leaves it alone. So far, the rapid and widespread infection has only been a nuisance. Until the second-stage payload arrives, any motive remains a mystery.
How Infected USB Drives Spread the Worm
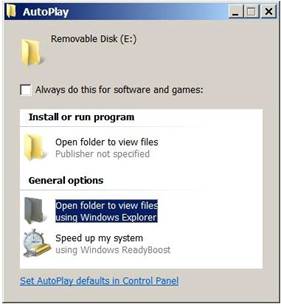 In theAutoplay dialog box image shown here, you can see two entries that both appear to display the contents of removable media by opening a folder to view files. But if you look closely, you will see that one of them is categorized as an option to “Install or run program.” This option to “Open folder to view files, Publisher not specified” has been added by the malware and, if selected, would execute its own infected program and begin spreading to other computers without human intervention. The second entry, which is highlighted under “General options,” says “Open folder to view files using Windows Explorer.” This one is the correct option and is harmless. In theAutoplay dialog box image shown here, you can see two entries that both appear to display the contents of removable media by opening a folder to view files. But if you look closely, you will see that one of them is categorized as an option to “Install or run program.” This option to “Open folder to view files, Publisher not specified” has been added by the malware and, if selected, would execute its own infected program and begin spreading to other computers without human intervention. The second entry, which is highlighted under “General options,” says “Open folder to view files using Windows Explorer.” This one is the correct option and is harmless.
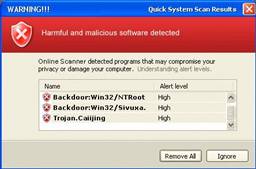
If you think you make have this worm and you’d like several choices for help, the Internet Storm Center of SANS.ORG has posted a complete list of third party removal tools and other information at isc.sans.org/diary.html?storyid=5860. However, it can be easily removed by using the Microsoft Windows Malicious Software Removal Tool. Microsoft releases an updated version of this tool on the second Tuesday of every month, or more often in response to security incidents. This tool is available from Microsoft Update, Windows Update, and the Microsoft Download Center. Or, if you’d prefer to run an online scanner, you can visit the Windows Live Protection Center.
Other Virus Concerns
New variants of another polymorphic and entry point obscuring (EPO) file infector, Virut, infect html and PE (portable executable) files. Once installed, this virus is designed to connect to an IRC (Internet Relay Chat) server, join a channel, and await instruction to download and execute arbitrary files. In some cases, however, errors in the code of Virut prevent it from working as designed, and instead produce corrupted infections beyond repair.
The newest variant of Mytob brought down the networks at three London hospitals recently, causing ambulances to be diverted to other facilities, backlogs of work, and delays in care and treatment. According to Symantec, this mass-mailing worm uses its own SMTP engine to send email to addresses gathered from the Windows Address Book on compromised computers, and also has the ability to open a back door and spread through the network.
How to Protect Yourself
The sad part about such widespread malware infections is that they are avoidable. The security company BeyondTrust recently analyzed all the security bulletins issued by Microsoft in 2008, and concluded that “92% of the critical vulnerabilities could have been mitigated” by configuring user accounts to operate without administrator rights. Even if you are the only user on your PC, you should still create such an account for yourself for everyday use and reserve an account with administrator privileges only when needed to install software or reconfigure your system. Never leave the administrator account logged in and unattended.
While corporate networks are most at risk for these types of infection, you can certainly bring the virus or worm to your home computer if you bring a flash drive from work. The delayed patch cycle implemented by most large companies allows their many computers to remain unprotected, and is the reason it’s so important to keep your own firewall and antivirus programs, as well as Windows, up to date. As soon as vulnerabilities are identified, patches are released to protect your computer. To avoid unintentionally downloading malware, you should never click links in unsolicited messages or click OK in warning boxes without reading them. Always download updates from known sources. And remember that the cybercriminals never quit trying to trick you.
Beverly Rosenbaum, a HAL-PC member, is a 1999 and 2000 Houston Press Club “Excellence in Journalism” award winner. Send her your comments about this column to columns@hal-pc.org.
|

